How It Works
Deploy Agents
Choose and deploy identity or scanner agents securely.
Create Workflows
Link agents to automate end-to-end validation workflows.
Validate Security
Get actionable findings and remediation insights.
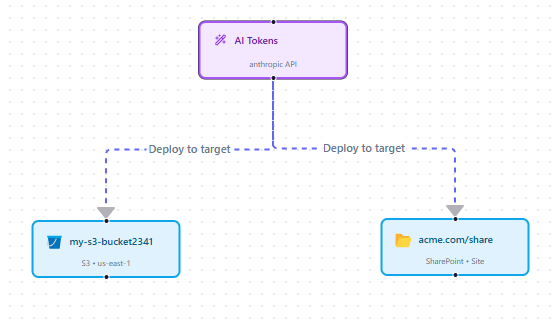
How You Build a Workflow
Visually connect identity, scanner, and deployment agents into secure validation pipelines. A single agent can fan out to multiple targets — like AWS S3, SharePoint, and Azure — for parallel testing and coverage.